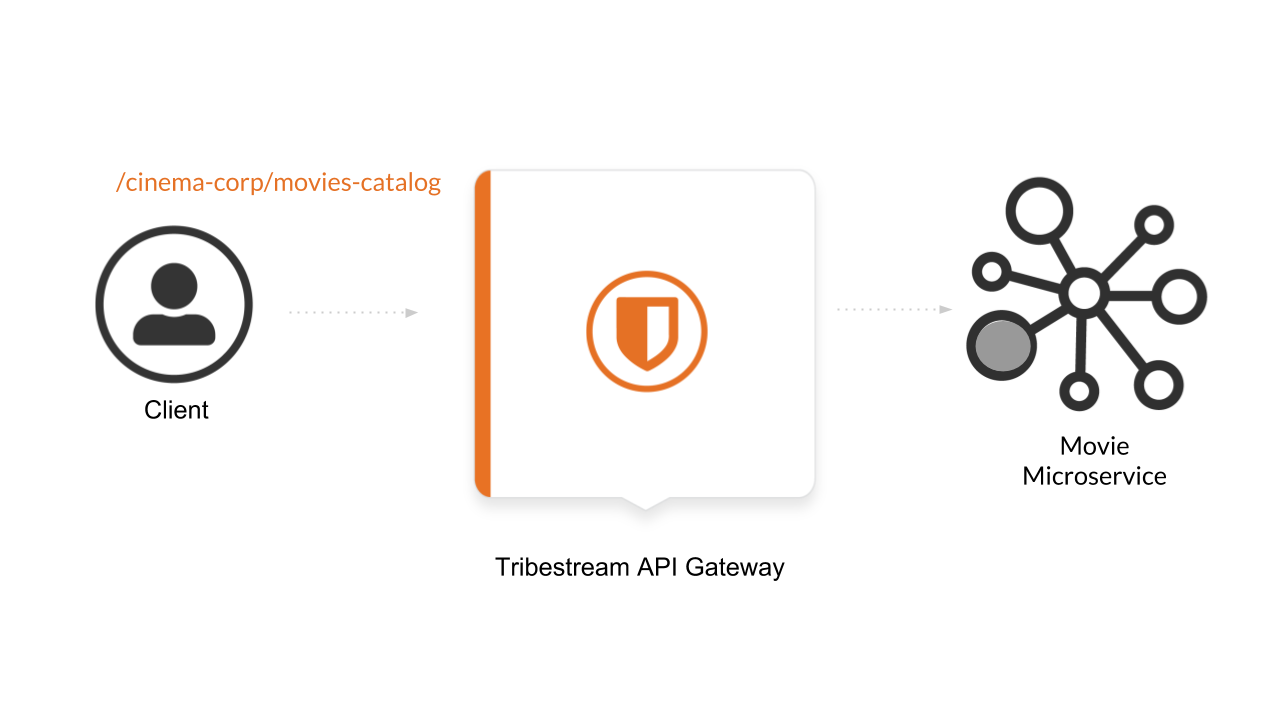
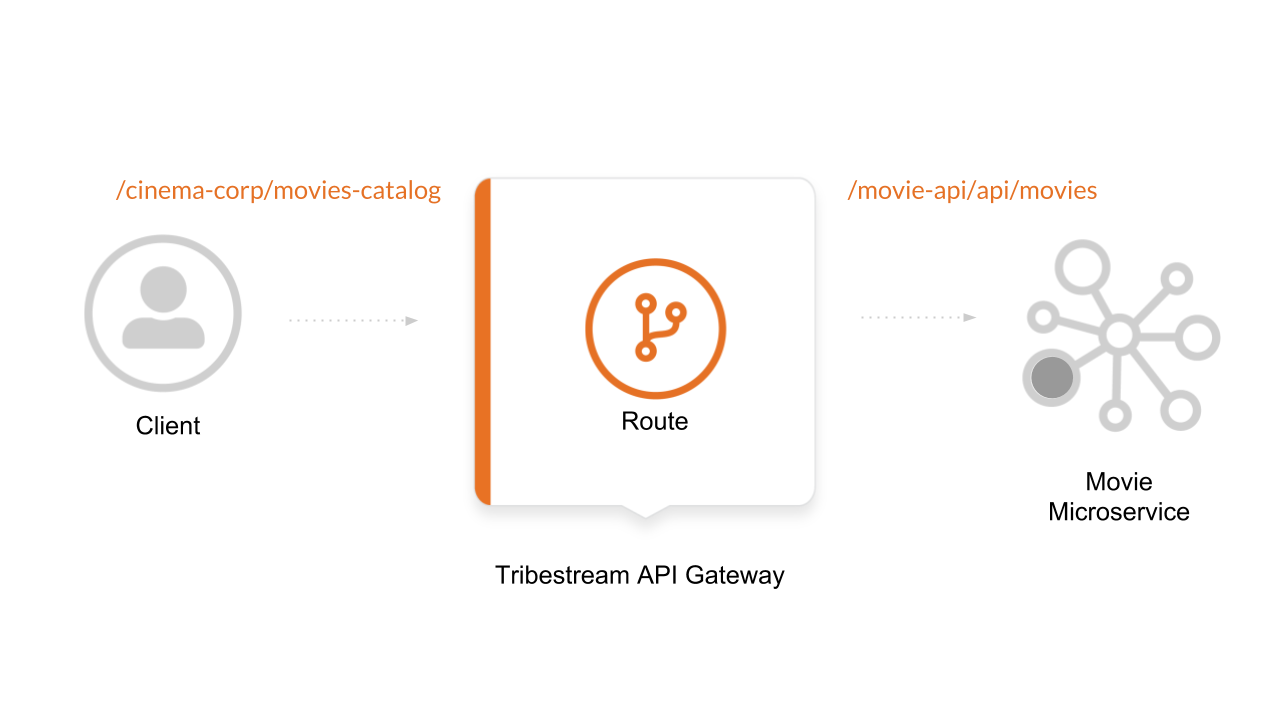
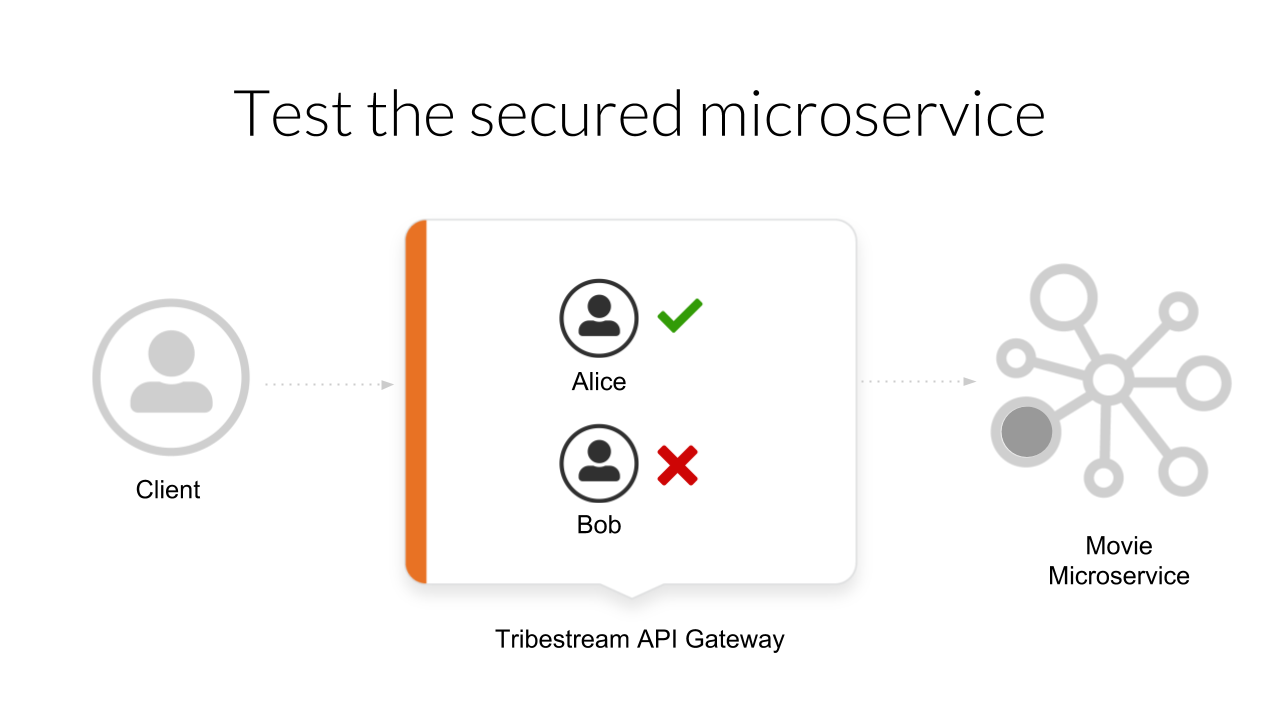
During this guide we are going to learn how to secure a microservice with authentication and authorization using the Tribestream API Gateway. In the diagram the main actors are:
A Client who want’s to consume a REST endpoint to list the movies catalog from the cinema corporation.
Tribestream API server who is securing the movie microservice with Authentication and Authorization.
A movie microservice that contains the list of available movies in it’s database.
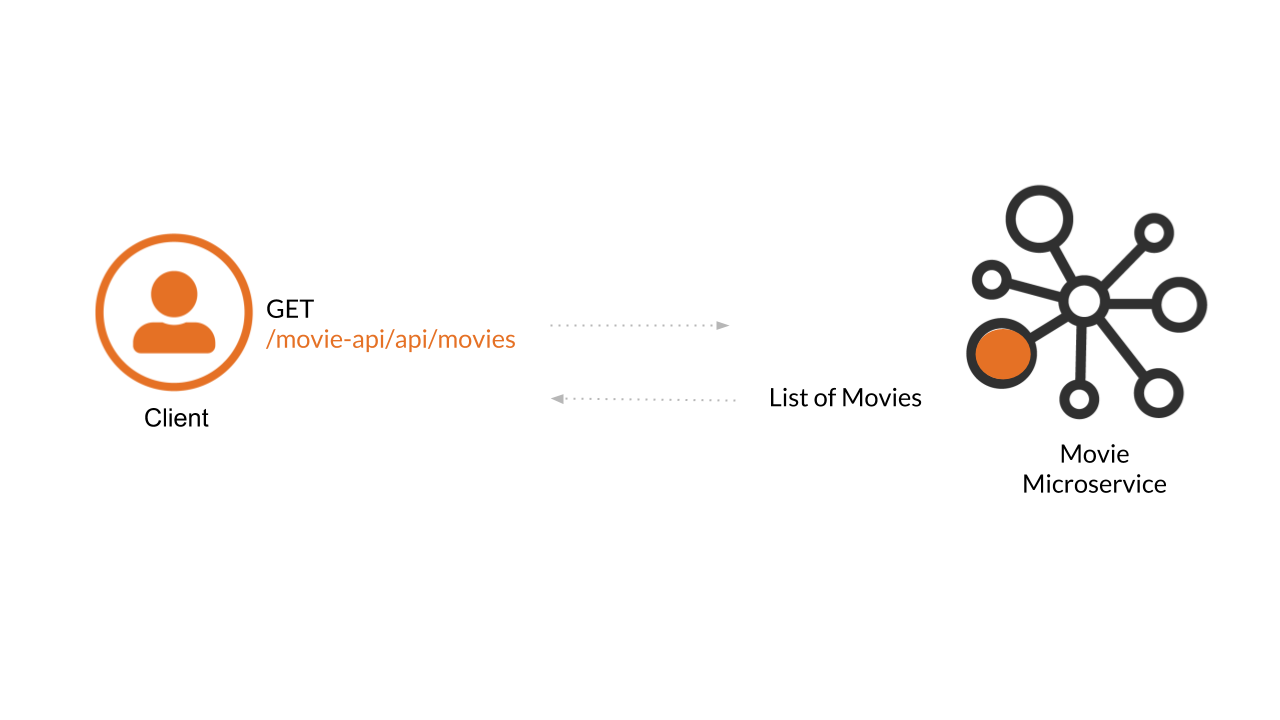
The following diagrams shows a client who obtain a list of movies form the microservice by executing a request to the movie-api/api/movies endpoint. Notice that at this point all the communication is done without security.
In order to run our demo microservice we need to open a terminal and execute the following command:
docker run -it -p 9090:9090 --name movie-api tomitribedev/movie-apiThe movie microservice is ready when you see the following message on the log:
> [email protected] start /usr/src/app
> node server.js
Running on http://0.0.0.0:9090To detach the container log output, type on the terminal: ctrl+p followed by ctrl+q
We can validate that our microservice is up and running by executing the following command:
curl -i http://localhost:9090/movie-api/api/moviesYou should be able to see the response obtained from the microservice, a 200 HTTP Code and a payload with the list of movies in JSON Format:
HTTP/1.1 200 OK
X-Powered-By: Express
Content-Type: application/json; charset=utf-8
Content-Length: 907
ETag: W/"38b-nH1wH3YovzhC6d7xYfLwUga8Hf8"
Date: Wed, 04 Jul 2018 17:19:33 GMT
Connection: keep-alive
[{"comments":[],"year":2008,"director":"Sylvester Stallone","genrer":"Action","rating":7,"id":2,"title":"John Rambo"},{"comments":[],"year":2008,"director":"Sylvester Stallone","genrer":"Action","rating":7,"id":52,"title":"John Rambo"},{"comments":[],"year":1999,"director":"Syl","genrer":"Sci-Fi","rating":9,"id":1,"title":"The Matrix"},{"comments":[],"year":1999,"director":"Syl","genrer":"Sci-Fi","rating":9,"id":51,"title":"The Matrix"},{"comments":[],"year":1997,"director":"Paul Verhoeven","genrer":"Sci-Fi","rating":7,"id":3,"title":"Starship Troopers"},{"comments":[],"year":1997,"director":"Paul Verhoeven","genrer":"Sci-Fi","rating":7,"id":53,"title":"Starship Troopers"},{"comments":[],"year":1994,"director":"Roland Emmerich","genrer":"Sci-Fi","rating":7,"id":4,"title":"Stargate"},{"comments":[],"year":1994,"director":"Roland Emmerich","genrer":"Sci-Fi","rating":7,"id":54,"title":"Stargate"}]The Tribestream API Gateway is going to seat between the Client and the Microservice in order to enforce Basic Auth security to the Microservice. Other TAG features like Advance Security, Routing, Load Balancing and Monitoring are cover later in the Learning Journey.
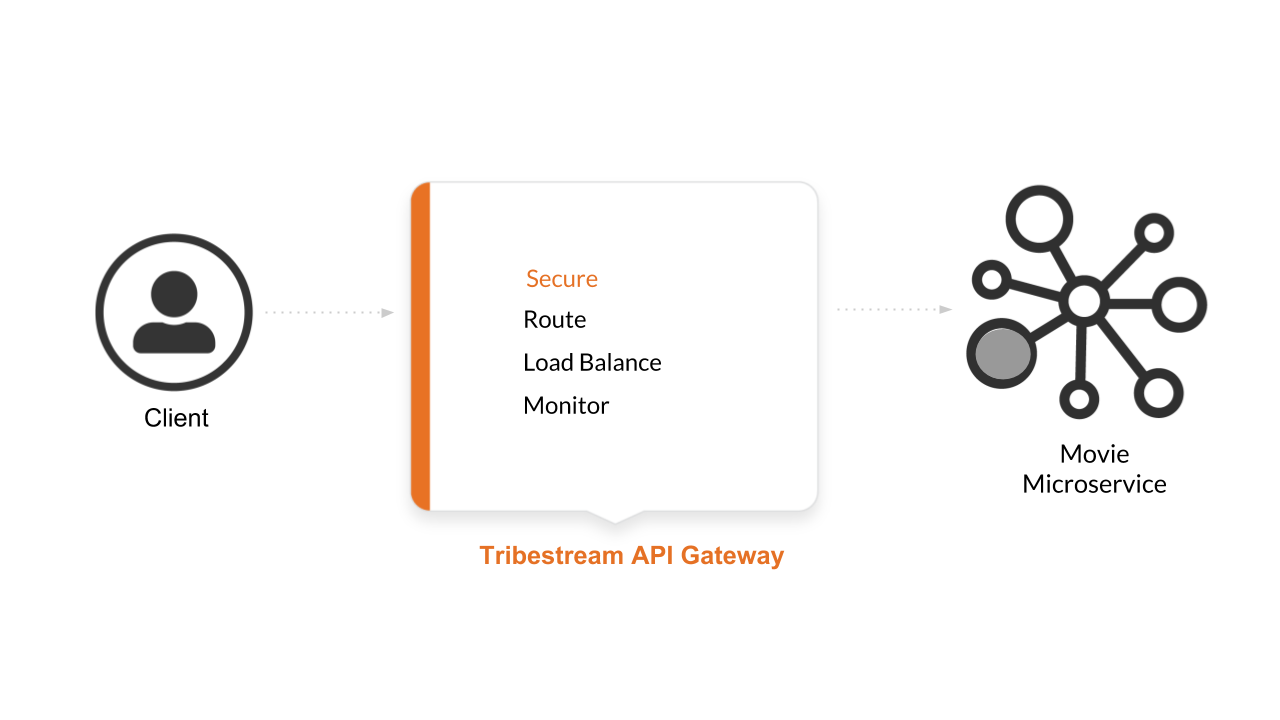
On a terminal execute the following command according to your operating system:
For linux:
docker run --net="host" -it -e LICENSE=accept --name tag tomitribe/tribestream-api-gatewayFor OSX or Windows:
docker run -it -e LICENSE=accept --name tag -p 8080:8080 tomitribe/tribestream-api-gatewayTAG is ready when you see the following message on the TAG log:
INFO [main] org.apache.coyote.AbstractProtocol.start Starting ProtocolHandler ["http-bio-8080"]
INFO [main] org.apache.coyote.AbstractProtocol.start Starting ProtocolHandler ["ajp-bio-8009"]
INFO [main] org.apache.catalina.startup.Catalina.start Server startup in 18348 msTo detach the TAG container log output, type on the terminal: ctrl+p followed by ctrl+q
Open a browser and navigate to: http://localhost:8080/tag
Login into the TAG dashboard using the following credentials:
username: admin
password: admin

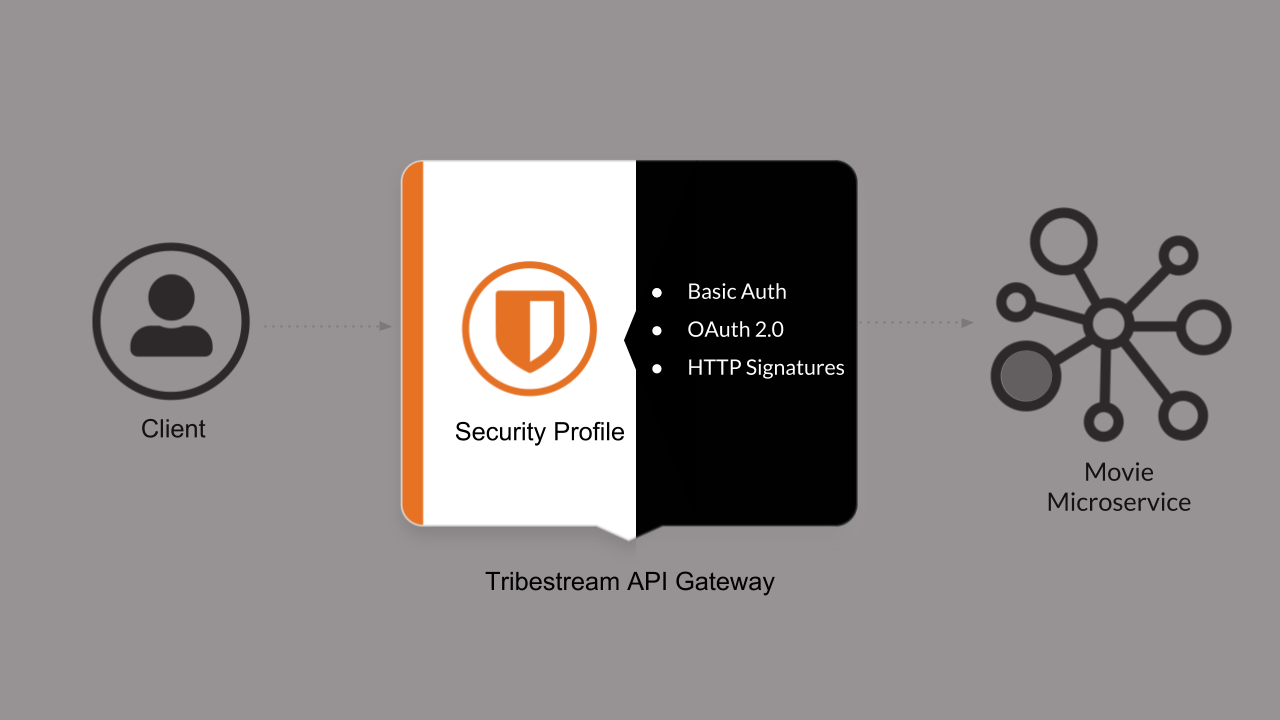
In order to secure the movie microservice we need to create a TAG Security Profile, for the purpose of demonstration we are going to use the built in Basic Auth Profile but we recommend stronger Authenticator such as OAuth 2 or HTTP Signatures which are shown later in the learning journey. For the authorization we are going to rely on TAG User Roles.
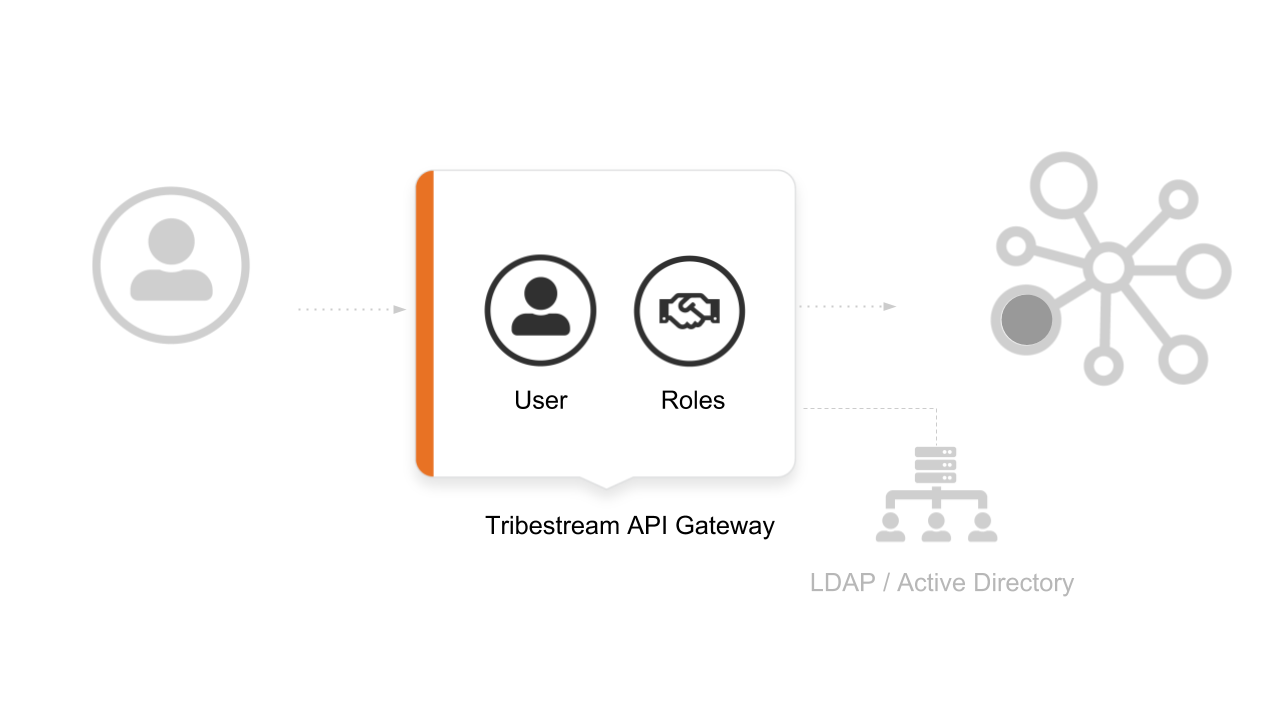
A client who want to access the microservice through the TAG, will require an Account with a User, valid credentials and one or more valid roles. We are going to create this entities right from the TAG UI but you can also use an authorization system like Ldap or Active Directory.
We are going to create two accounts in TAG, Alice is going to have the administrator role
and Bob the user role.
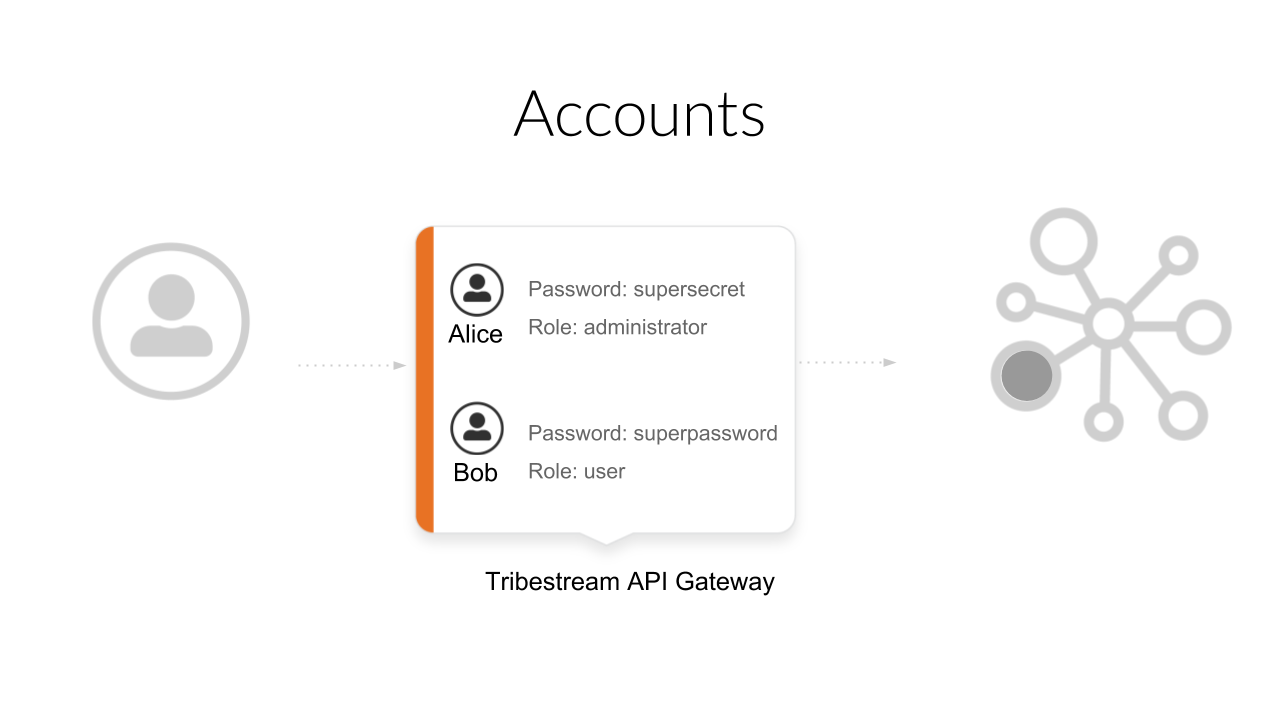
To create the two accounts we are going to use to authenticate and authorize the deployed microservices, follow the next steps:
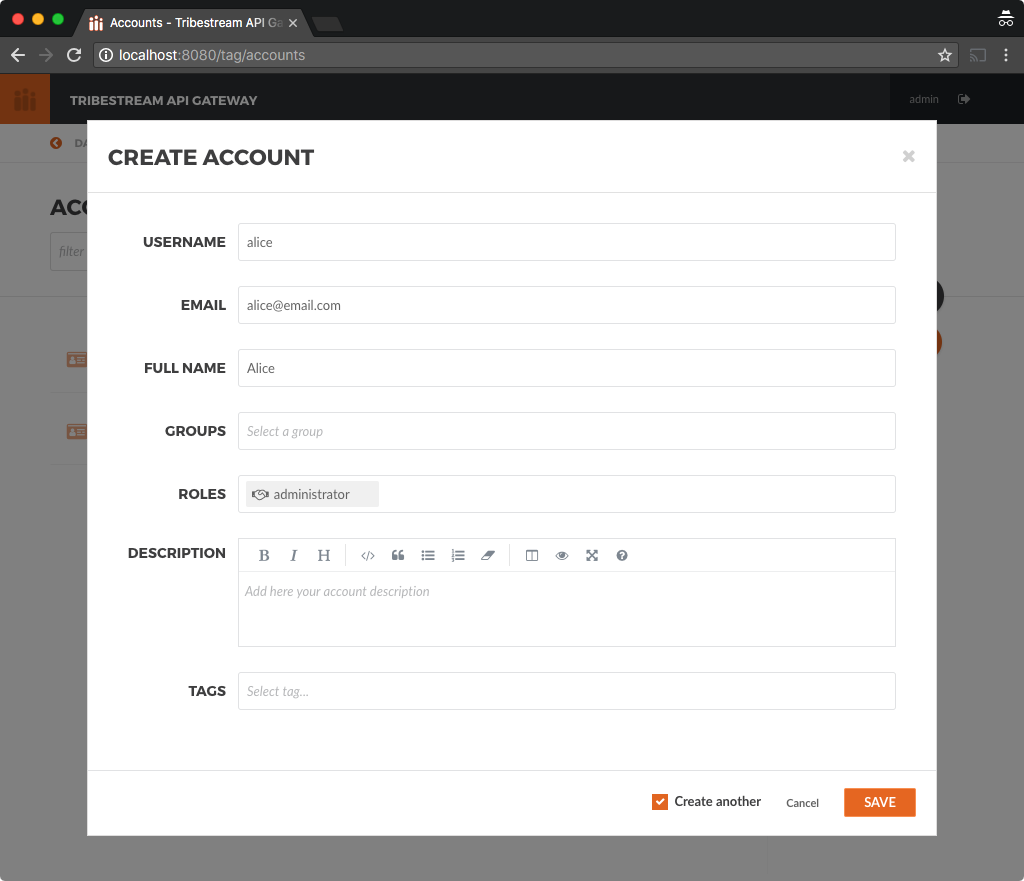
Click on the Accounts option to navigate to Accounts page, click the + button on the upper right side and
select Account. Create a new account with the following data and make sure you enable the Create another check
box before clicking the Save button.
Notice that the administrator role is automatically created and assigned to Alice when you create the account.
Username: alice
Email: [email protected]
Fullname: Alice
Roles: administrator
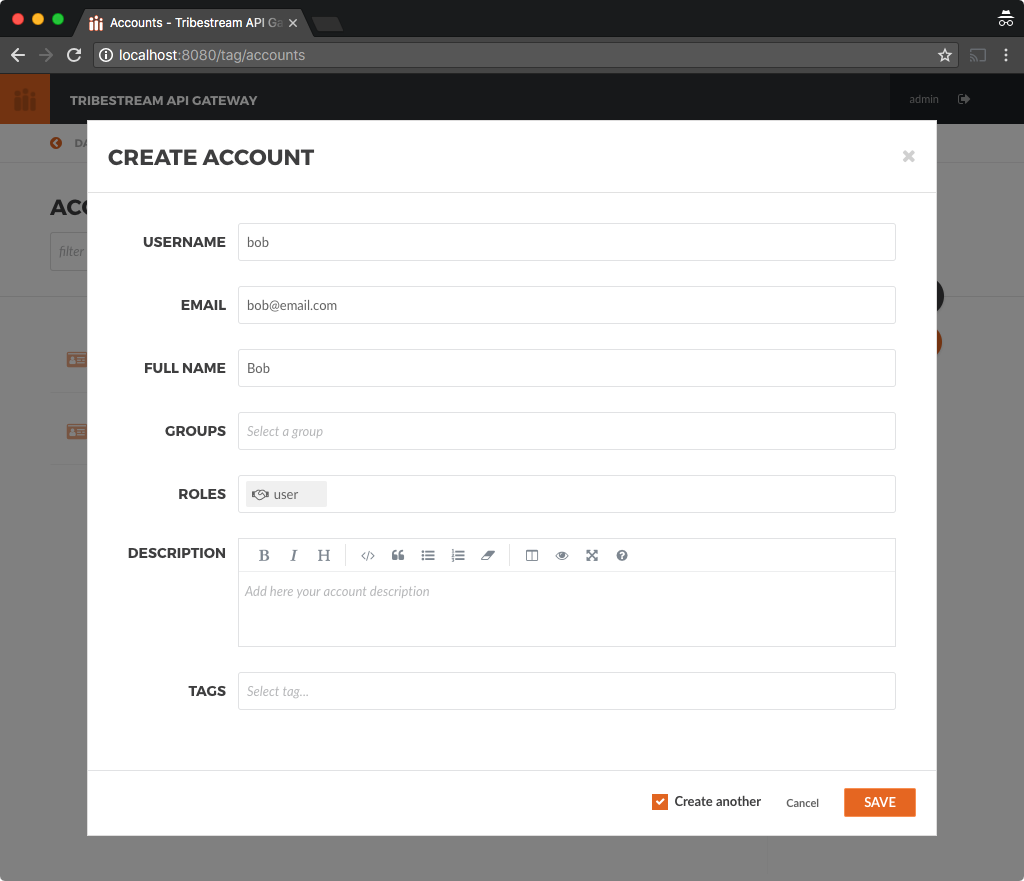
For the second account use the following data.
Username: bob
Email: [email protected]
Fullname: Bob
Roles: user
Notice that Bob account only needs to have the role user.
After filling in the data click Save button and then close the Create Account modal window.
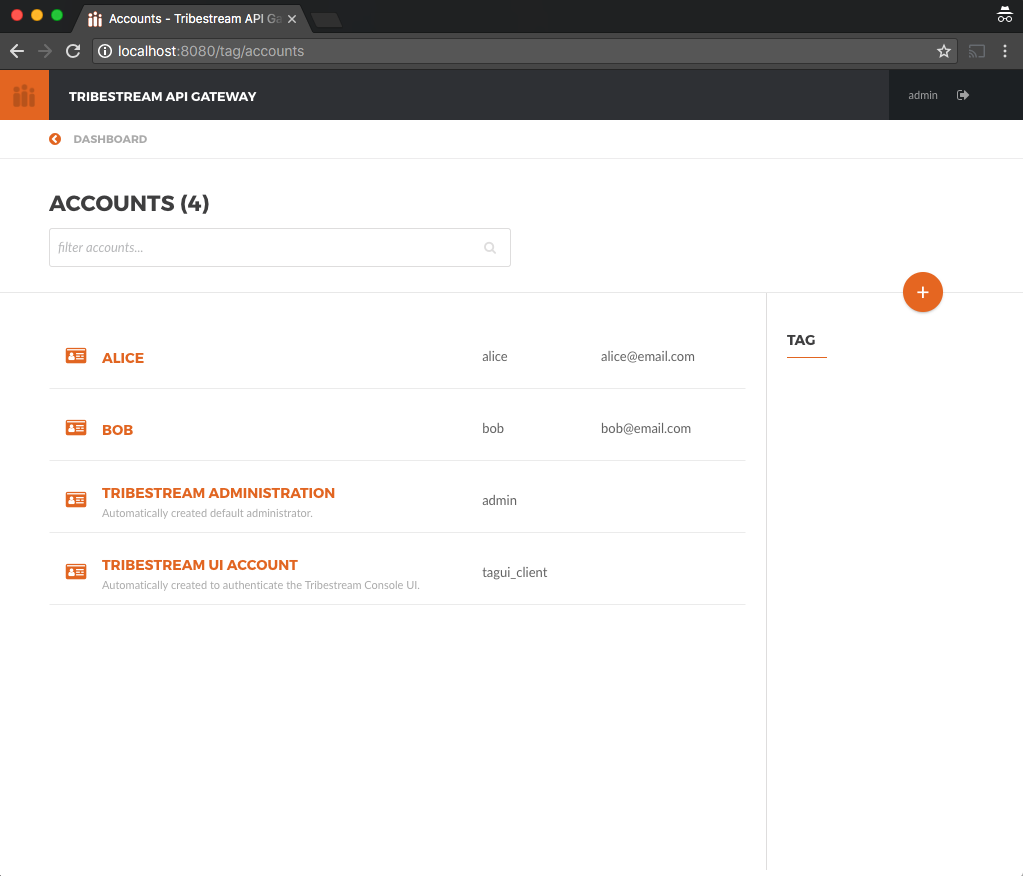
You should be able to see the two accounts as part of the list displayed on the Accounts page.
Now we are going to assign a basic auth password to both accounts.
From the Accounts page, click on Alice account to open the account detail page.
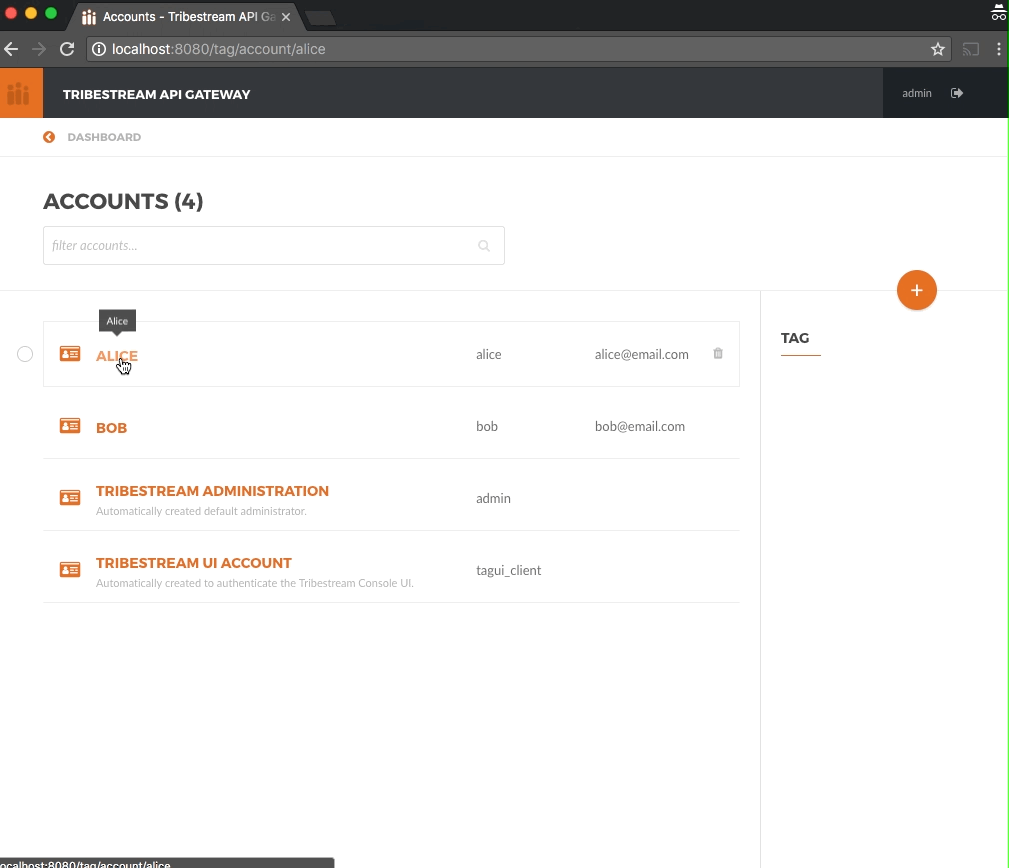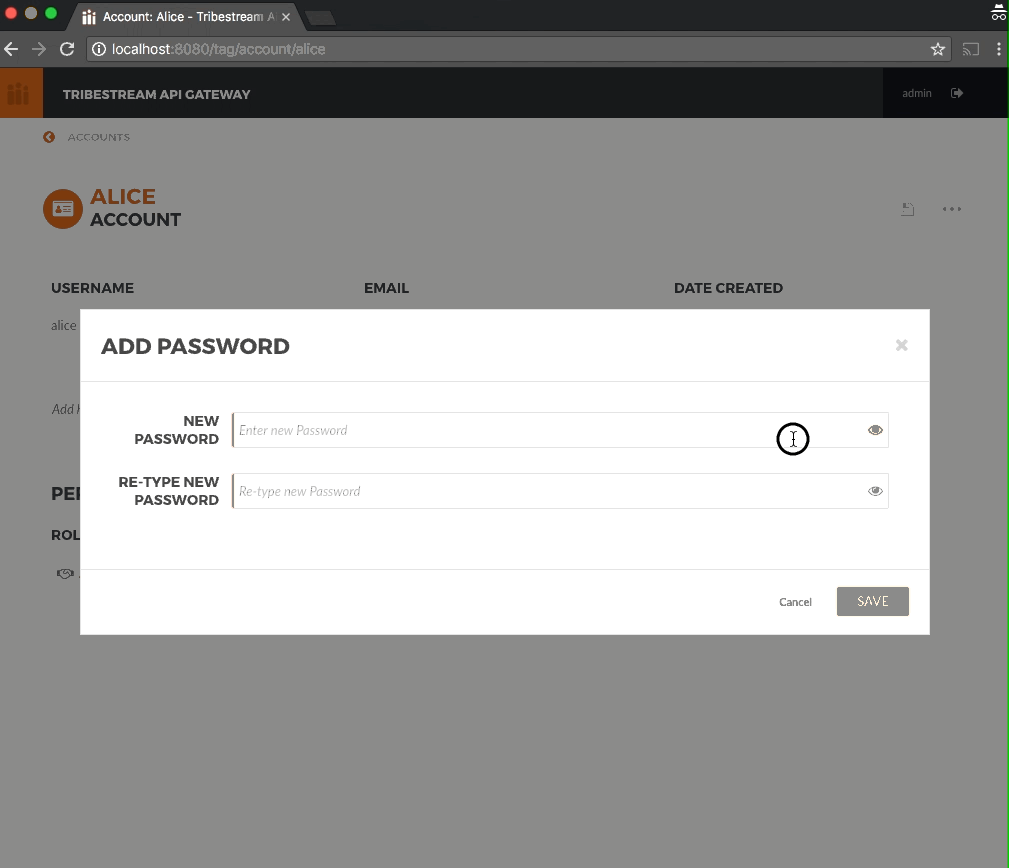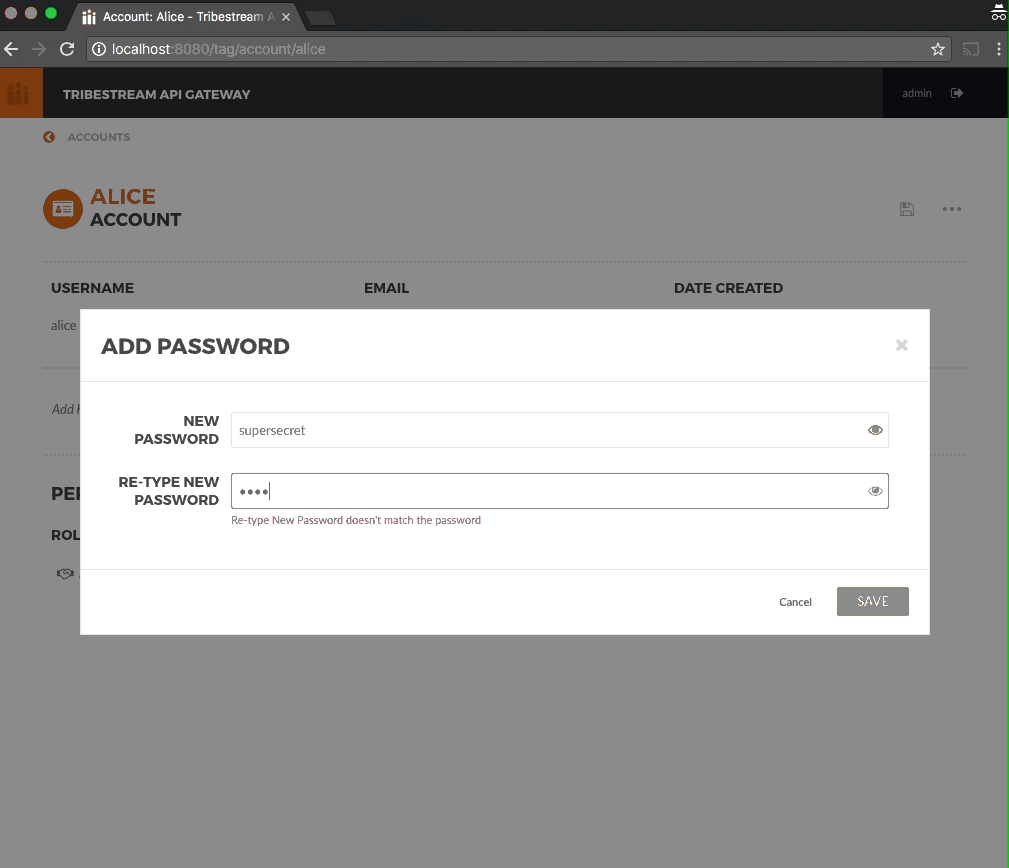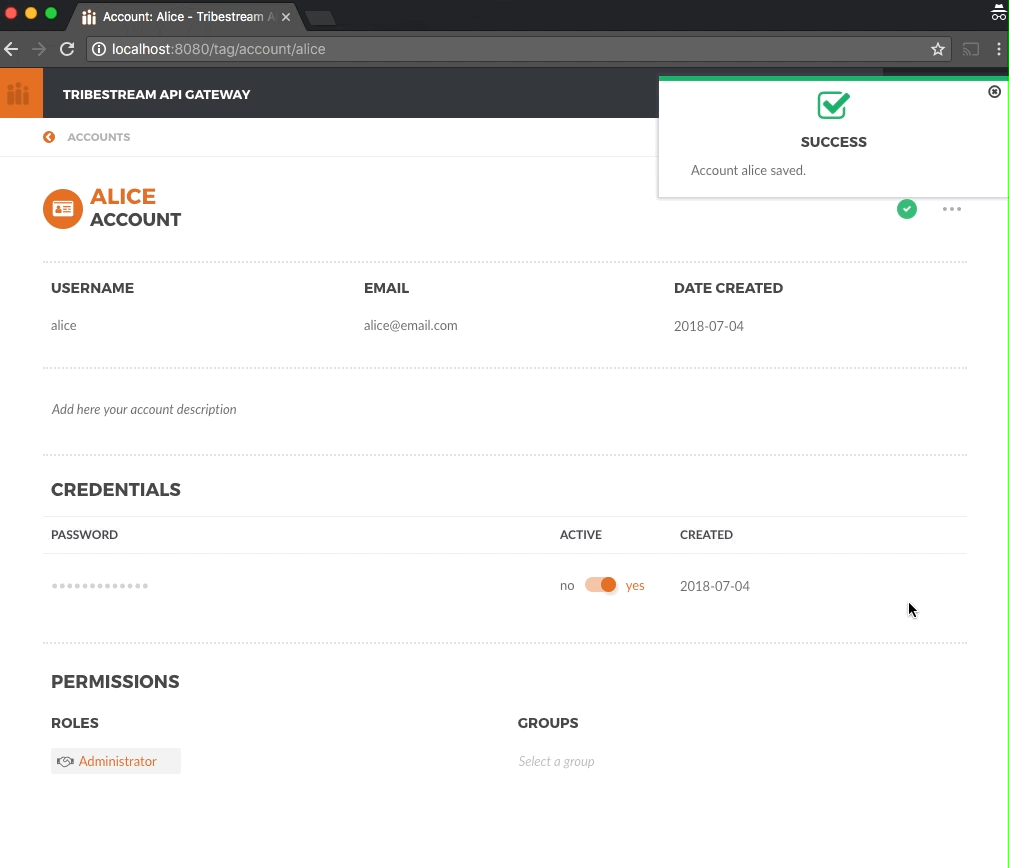
Click the … button on the upper right side and select Add Password from the menu. In the Add Password modal window,
type supersecret as the password and then click the Save button.
From Alice account deail page go back to Accounts page by doing a click on the < ACCOUNTS option in the upper left corner and repeat the previous steps to add superpassword as the password for Bob account.
From Bob account detail page, click the Tribestream API Gateway home icon located on the upper left corner of the screen
to navigate back to the Dashboard page.
The mechanism used by the Tribestream API Gateway (TAG) to orchestrate and secure the traffic to and from API endpoints is called Route.
We need to create a Route that will expose in TAG a /cinema-corp/movies-catalog endpoint, that will enforce Authentication (Basic Auth) and Authorization (via administrator role) for incoming requests before routing to the actual /movie-api/api/movies endpoint.
From the Dashboard page, click the Route button and then from the Routes page click the + button on the upper right
side and select Mod_Rewrite Route.
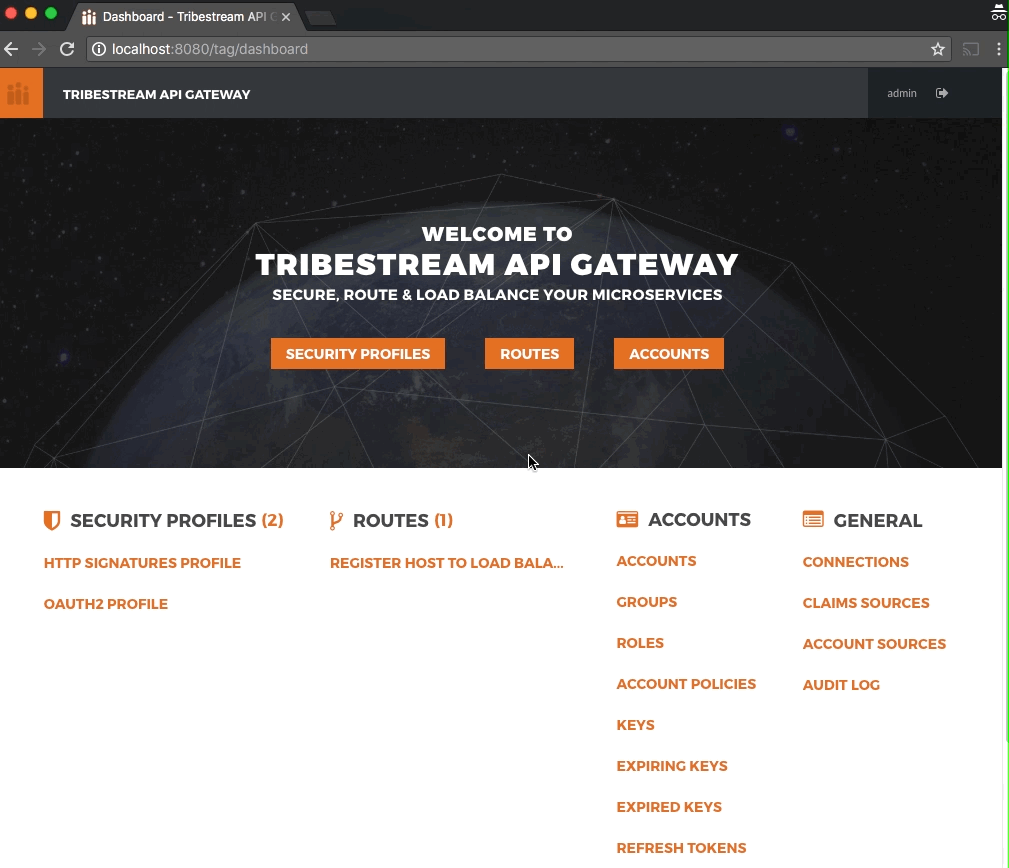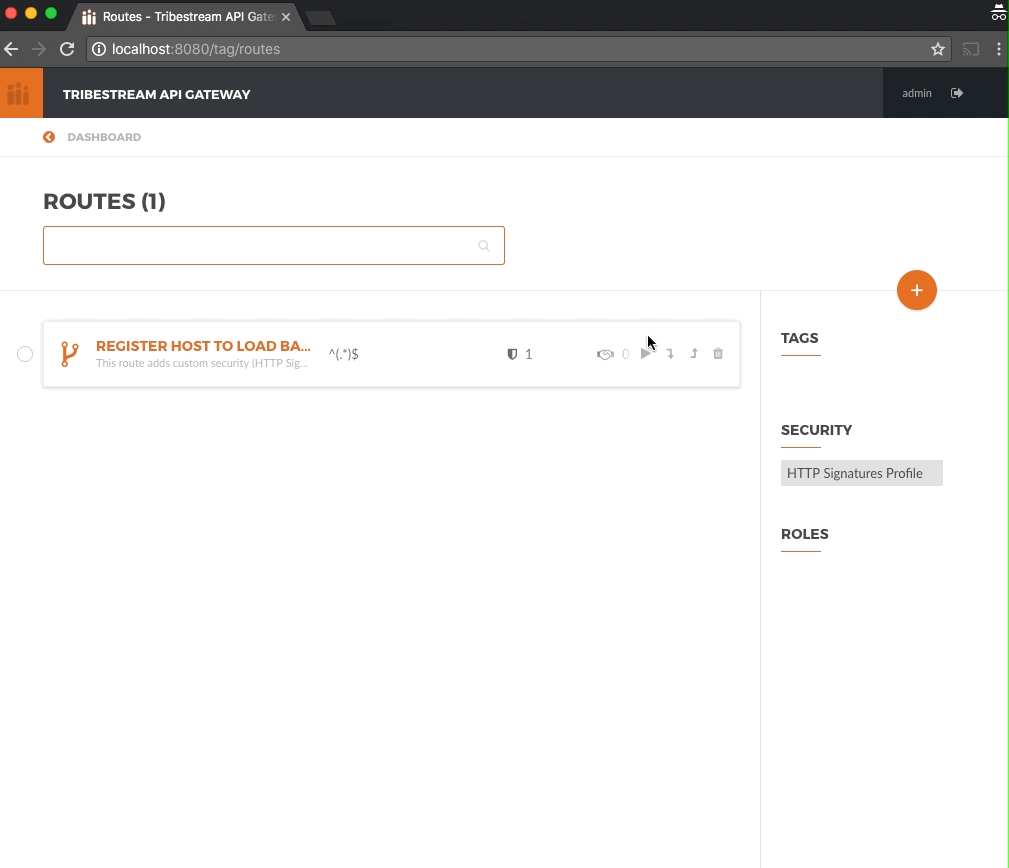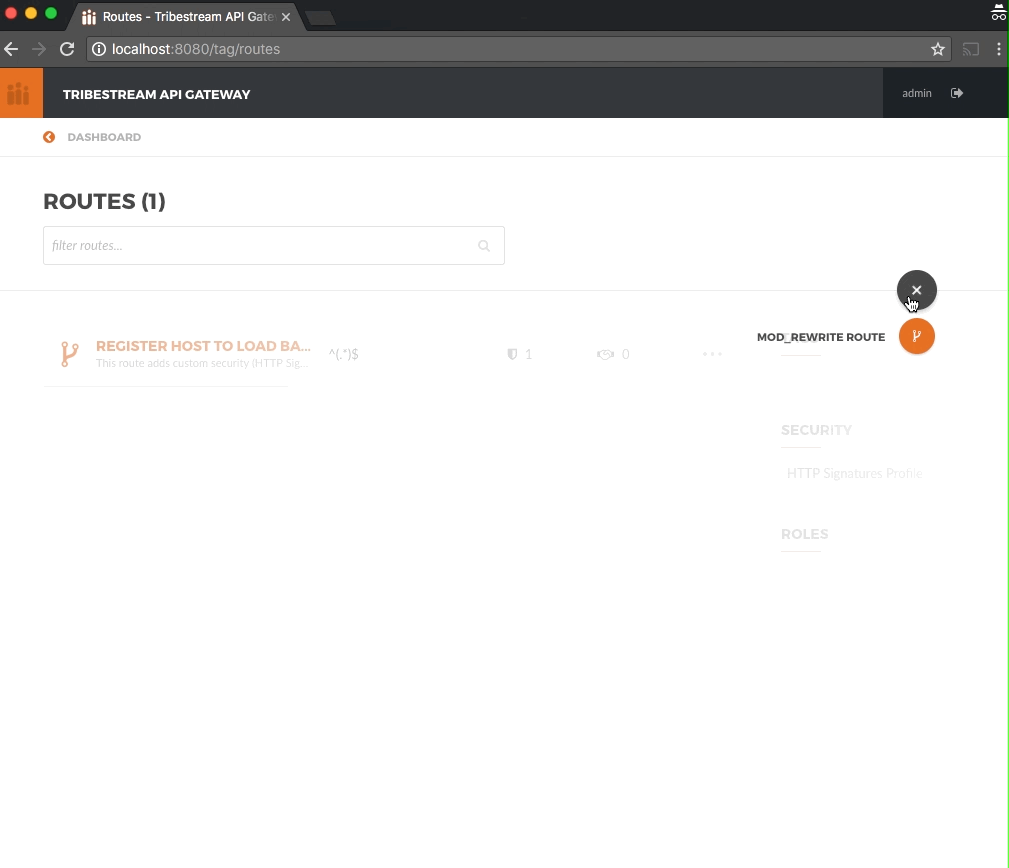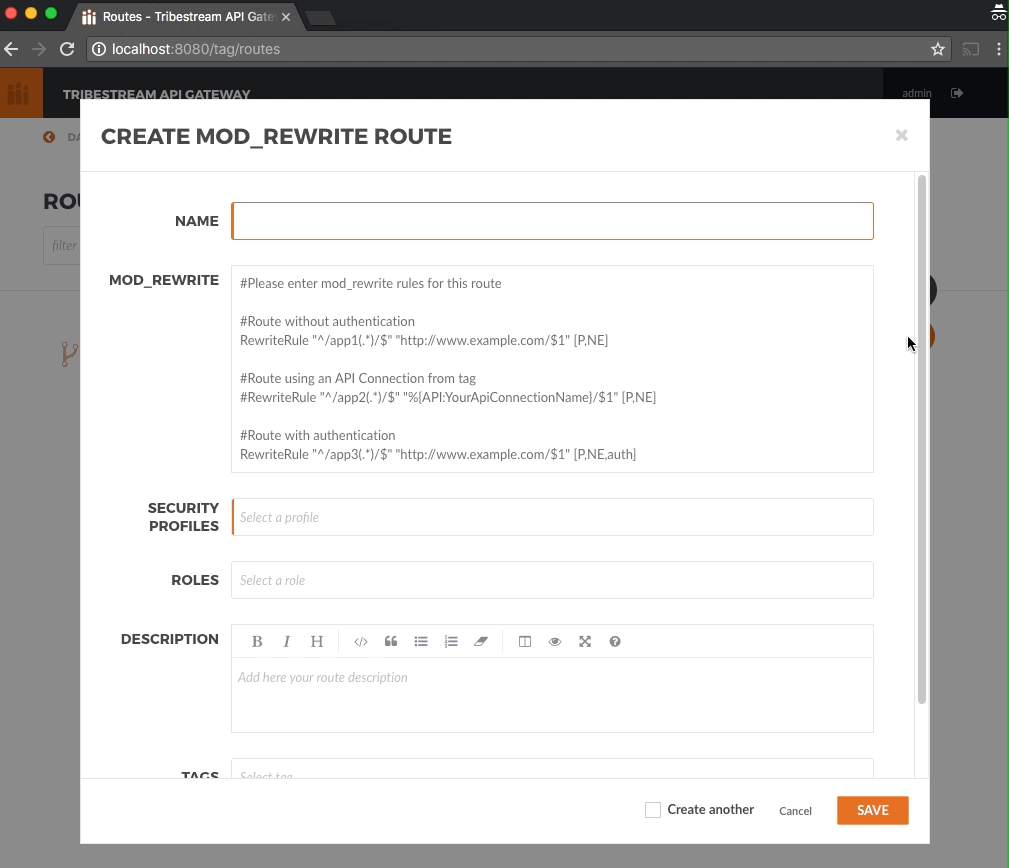
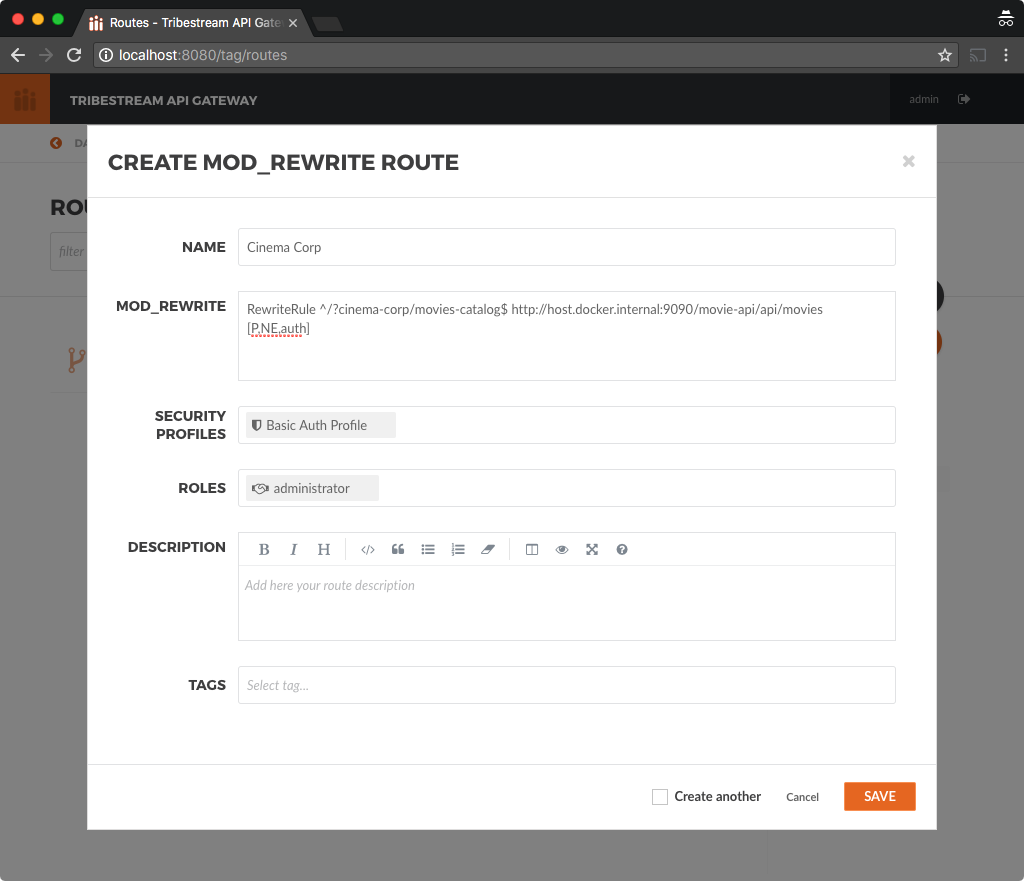
Create a new Route with the following data and click Save:
Name: Cinema Corp
Mod_Rewrite:
For linux:
RewriteRule ^/?cinema-corp/movies-catalog$ http://localhost:9090/movie-api/api/movies/ [P,NE,auth]
For OS X and Windows:
RewriteRule ^/?cinema-corp/movies-catalog$ http://host.docker.internal:9090/movie-api/api/movies [P,NE,auth]
Security Profile: Basic Auth Profile
Roles: administrator
If you want to know more about the mod_rewrite syntax, we have more guides in the Learning Journey that will explains the syntax with details and examples.
But for now we need to emphasize that the route we created is going to provide the endpoint /cinema-corp/movies-catalog in TAG and internally is going to redirect incoming request to the microservice if and only if the Authentication and Authorization is the right one in the incoming request.
To successfully test the secured microservice you can use Alice account because it already contains the required
administrator role. We are going to use curl command to send a GET request to the TAG endpoint /cinema-corp/movies-catalog we configured on the route and we are going to use basic auth to authenticate and authorize Alice request.
On a terminal the following command.:
curl -i -u alice:supersecret http://localhost:8080/cinema-corp/movies-catalogYou should be able to see the TAG response with a 200 HTTP code and the microservice payload:
HTTP/1.1 200 OK
Access-Control-Allow-Origin: *
Access-Control-Allow-Headers: origin, content-type, accept, authorization, Etag, if-none-match, x-xsrf-token
Access-Control-Allow-Credentials: true
Access-Control-Allow-Methods: GET, POST, PUT, DELETE, OPTIONS, HEAD
Access-Control-Max-Age: 1209600
Access-Control-Expose-Headers: origin, content-type, accept, authorization, ETag, if-none-match
X-Proxy-Do-Rewrite: 6277575
X-Request-ID: bb629a0c5a4959da
X-Proxy-Received-HTTP-Status: 200
X-Proxy-Elapsed: 534119396
X-Powered-By: Express
ETag: W/"38b-nH1wH3YovzhC6d7xYfLwUga8Hf8"
Content-Type: application/json;charset=utf-8
Transfer-Encoding: chunked
Date: Thu, 02 Aug 2018 18:53:00 GMT
Server: Tomitribe-TAG
[{"comments":[],"year":2008,"director":"Sylvester Stallone","genrer":"Action","rating":7,"id":2,"title":"John Rambo"},{"comments":[],"year":2008,"director":"Sylvester Stallone","genrer":"Action","rating":7,"id":52,"title":"John Rambo"},{"comments":[],"year":1999,"director":"Syl","genrer":"Sci-Fi","rating":9,"id":1,"title":"The Matrix"},{"comments":[],"year":1999,"director":"Syl","genrer":"Sci-Fi","rating":9,"id":51,"title":"The Matrix"},{"comments":[],"year":1997,"director":"Paul Verhoeven","genrer":"Sci-Fi","rating":7,"id":3,"title":"Starship Troopers"},{"comments":[],"year":1997,"director":"Paul Verhoeven","genrer":"Sci-Fi","rating":7,"id":53,"title":"Starship Troopers"},{"comments":[],"year":1994,"director":"Roland Emmerich","genrer":"Sci-Fi","rating":7,"id":4,"title":"Stargate"},{"comments":[],"year":1994,"director":"Roland Emmerich","genrer":"Sci-Fi","rating":7,"id":54,"title":"Stargate"}]You can now test the secured microservice using Bob account. This time TAG is going to deny access to the microservice
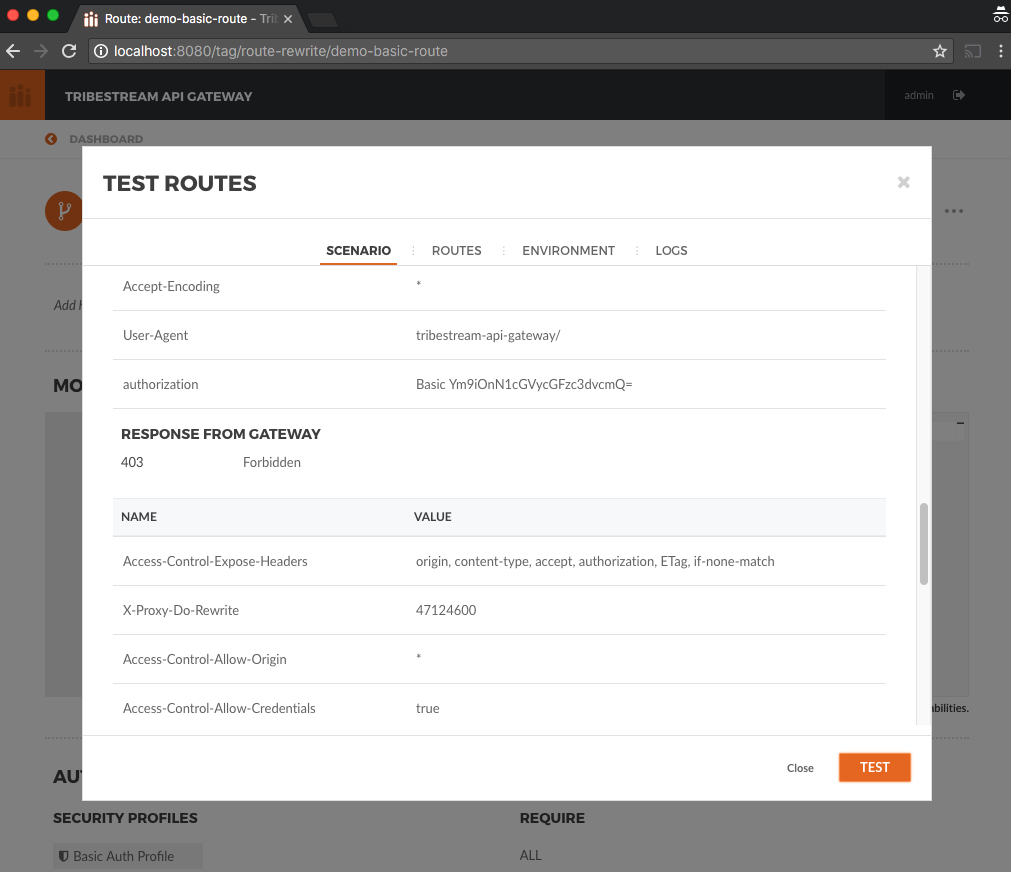
because Bob doesn’t have the administrator role. Execute the following command:
curl -i -u bob:superpassword http://localhost:8080/cinema-corp/movies-catalogYou should be able to see the TAG response with at 403 HTTP code:
HTTP/1.1 403 Forbidden
Access-Control-Allow-Origin: *
Access-Control-Allow-Headers: origin, content-type, accept, authorization, Etag, if-none-match, x-xsrf-token
Access-Control-Allow-Credentials: true
Access-Control-Allow-Methods: GET, POST, PUT, DELETE, OPTIONS, HEAD
Access-Control-Max-Age: 1209600
Access-Control-Expose-Headers: origin, content-type, accept, authorization, ETag, if-none-match
X-Proxy-Do-Rewrite: 5416110
X-Request-ID: 32b385417e7ead74
Content-Type: application/json;charset=ISO-8859-1
Content-Language: en
Content-Length: 64
Date: Thu, 02 Aug 2018 18:54:04 GMT
Server: Tomitribe-TAG
{"error":"Access to the specified resource has been forbidden."}You can also test the TAG routing, authentication and authorization right from the Cinema Corp Route detail page.
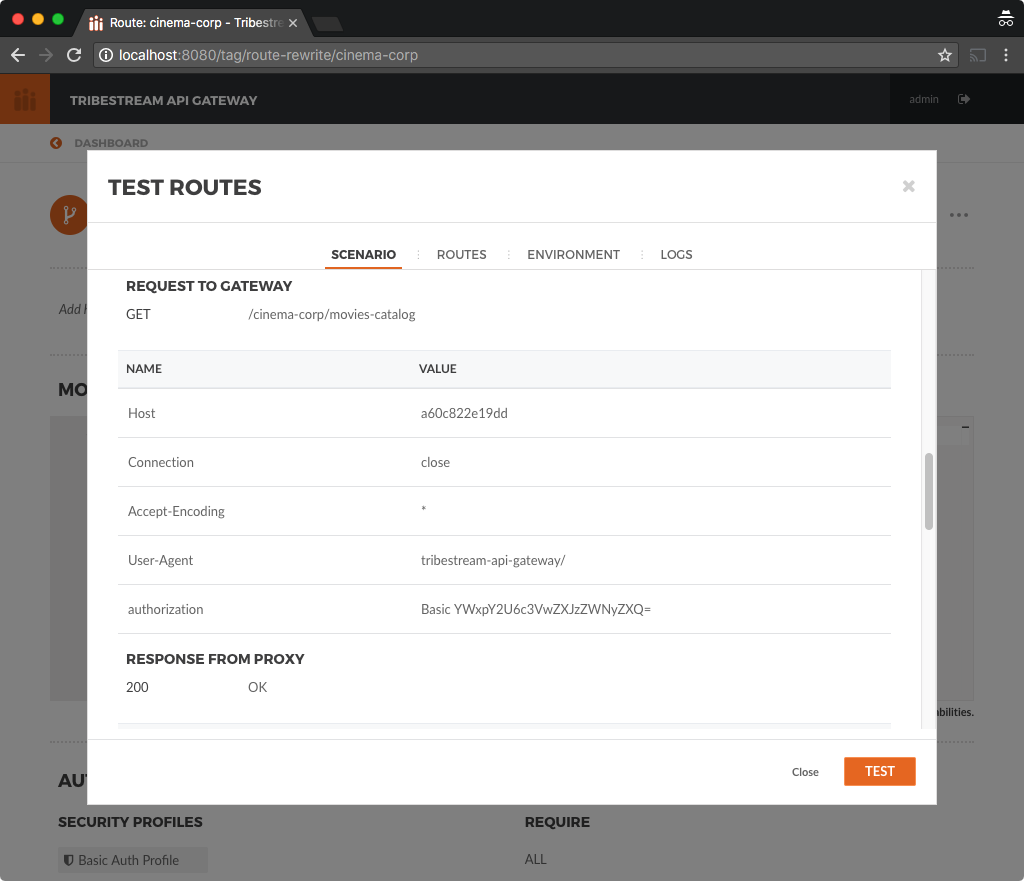
For this you need to open the Test Routes window by clicking the … button at the top right corner and then selecting
the Test option.
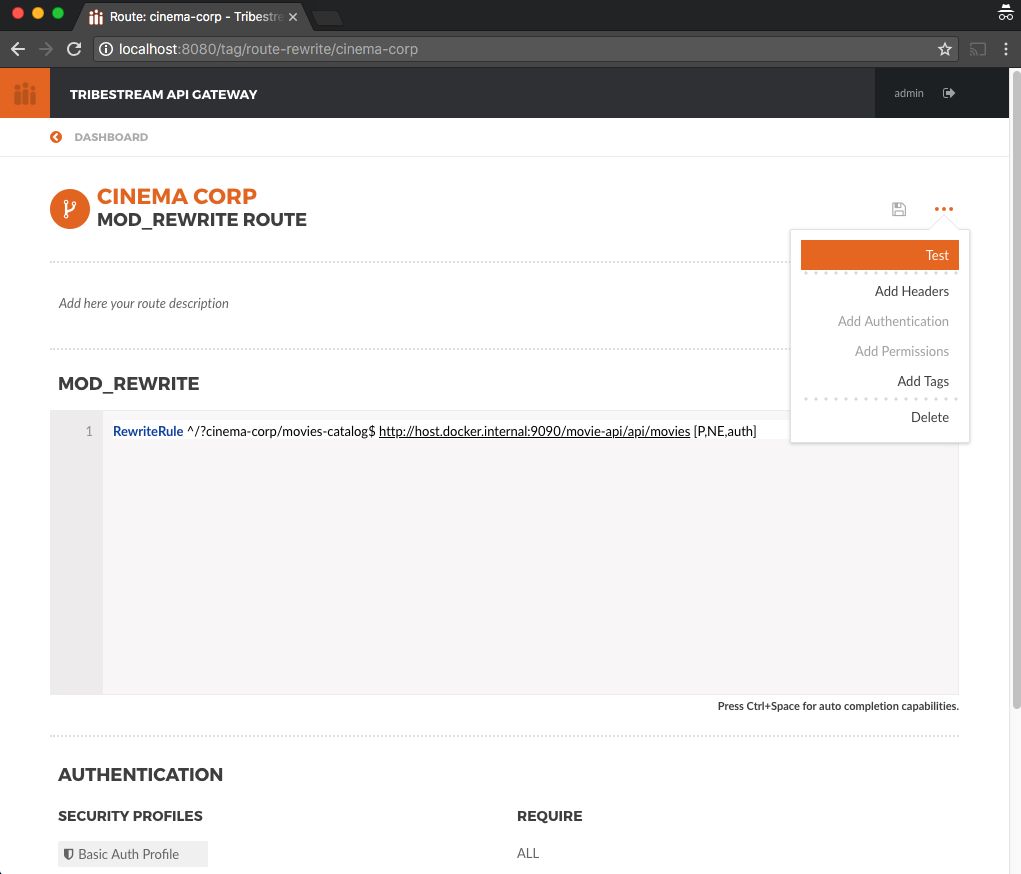
In the Test Routes window click the … button and select Add Basic Auth. Then add the following information and
click the Test button:
Resource URL: /cinema-corp/movies-catalog
Username: alice
Password: supersecreet
You will be able to see the 200 HTTP Response code along with details about the routing applied by TAG for the requests.
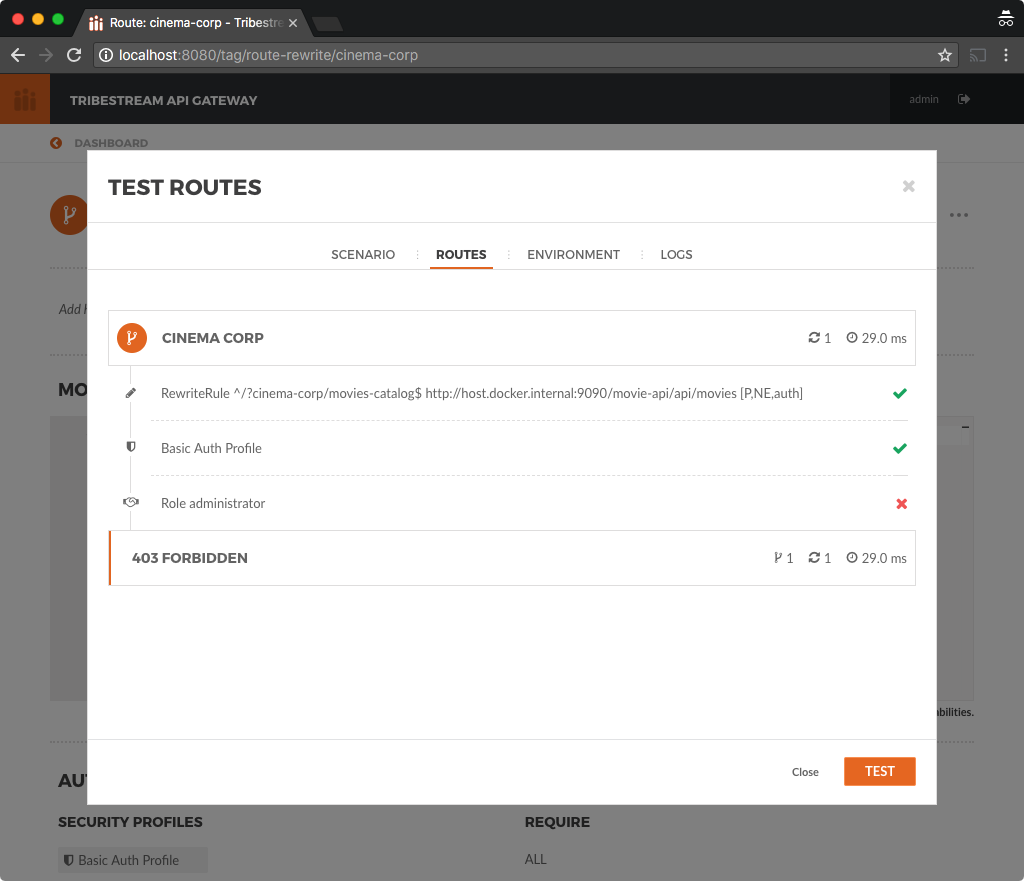
In the same Test Routes windows we can now execute a request using Bob account using the following information:
Resource URL: /cinema-corp/movies-catalog
Username: bob
Password: superpassword
This time you will see the 403 HTTP response code along with the details about the routing applied by TAG for the requests.